In this article we discuss why third-party risk managers and procurements professionals should monitor cloud storage containers as part of their ongoing supplier risk management strategy.
To many, the term ‘cloud storage containers’ (often referred to as “buckets”), is something that IT deals with, However, as we now live in a hyper-connected economy the protection of a business is the responsibility of a number of different teams. In fact, the whole business has a role in ensuring their organisation is secure. Even more so, those professionals whose role it is to onboard, monitor and maintain relationships with third-parties and suppliers.
Over the last five years cloud storage providers have seen exponential growth as business’s shift from costly-on premise IT infrastructure to the cloud hosted services. The likes of Amazon AWS, Google Cloud Platform and Microsoft Azure offer businesses the flexibility and scalability whilst also being cost-effective. But with any change and growth, comes risk.
In general, cloud hosted services default to a safe and secure mode of operation, however the configuration of many services is complex and responsibility usually resides with the client Their simplicity in design means it is easy for them to be mis-configured, either by accident or by users not fully understanding the knock-on effect of a configuration update. With a simple click critical services could be taken down or sensitive data leaked.
Public Cloud Buckets
Cloud storage containers have very flexible protection controls which means who or even what can access the data within the container can be controlled depending on the required use case. For example, bucket storage can be used to host personal details of employees and customers – which requires strict privacy controls; or host publicly available website content. Both valid uses.
In recent years there has been many examples of data breaches as a result of incorrectly configured buckets – with notable examples from Amazon S3. For example the Sennheiser data breach in December 2021 where it was reported that the audio manufacturing company exposed personal data of 28000 customers details with ‘leaky’ S3 buckets.
Third-party cloud storage risk
It is increasingly likely that many of a company’s third-parties – no matter how small – rely on some form of cloud storage, and with this comes increased risk
to the organisation. Complexities in the configuration of cloud storage and poor practices mean that critical business data may be left exposed, such that a bad actor can access potentially sensitive information without needing any special tools or techniques.
Being confident in your own business’ cloud storage security is one thing, but can organisations be confident that their third-parties hold themselves to the same rigorous security measures?
Understanding this risk and having continuous monitoring solutions in place will assist in maintaining a secure digital ecosystem and give organisations the ability to react quickly to any changes.
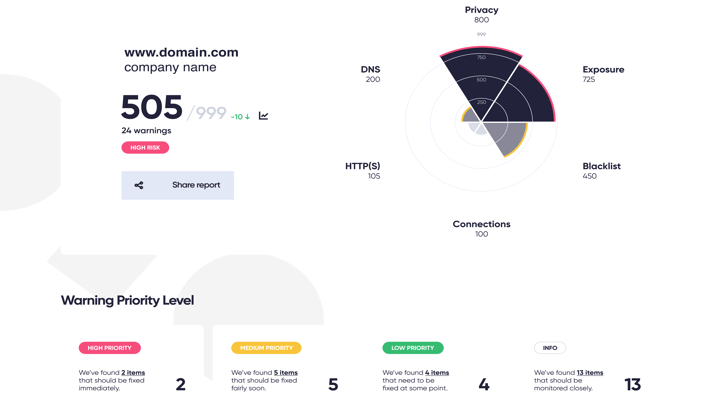
Using Darkbeam Horizon for third-party cyber risk monitoring will inform you whether a supplier has any public cloud storage buckets. It will also confirm if those storage buckets are secure or otherwise. We have seen this on a number of

occasions, where financial or even HR data has been left exposed and unencrypted.
In seconds of entering a domain Horizon will display critical an organisation’s digital risk profile for you to assess including cloud storage. Furthermore, with the creation of Watchlists, continuously monitor any changes to your digital ecosystem. Having this reassurance will ensure relationships are maintained and digital risk is reduced.
To start monitoring your suppliers cloud storage risk sign up to your free myHorizon account today.